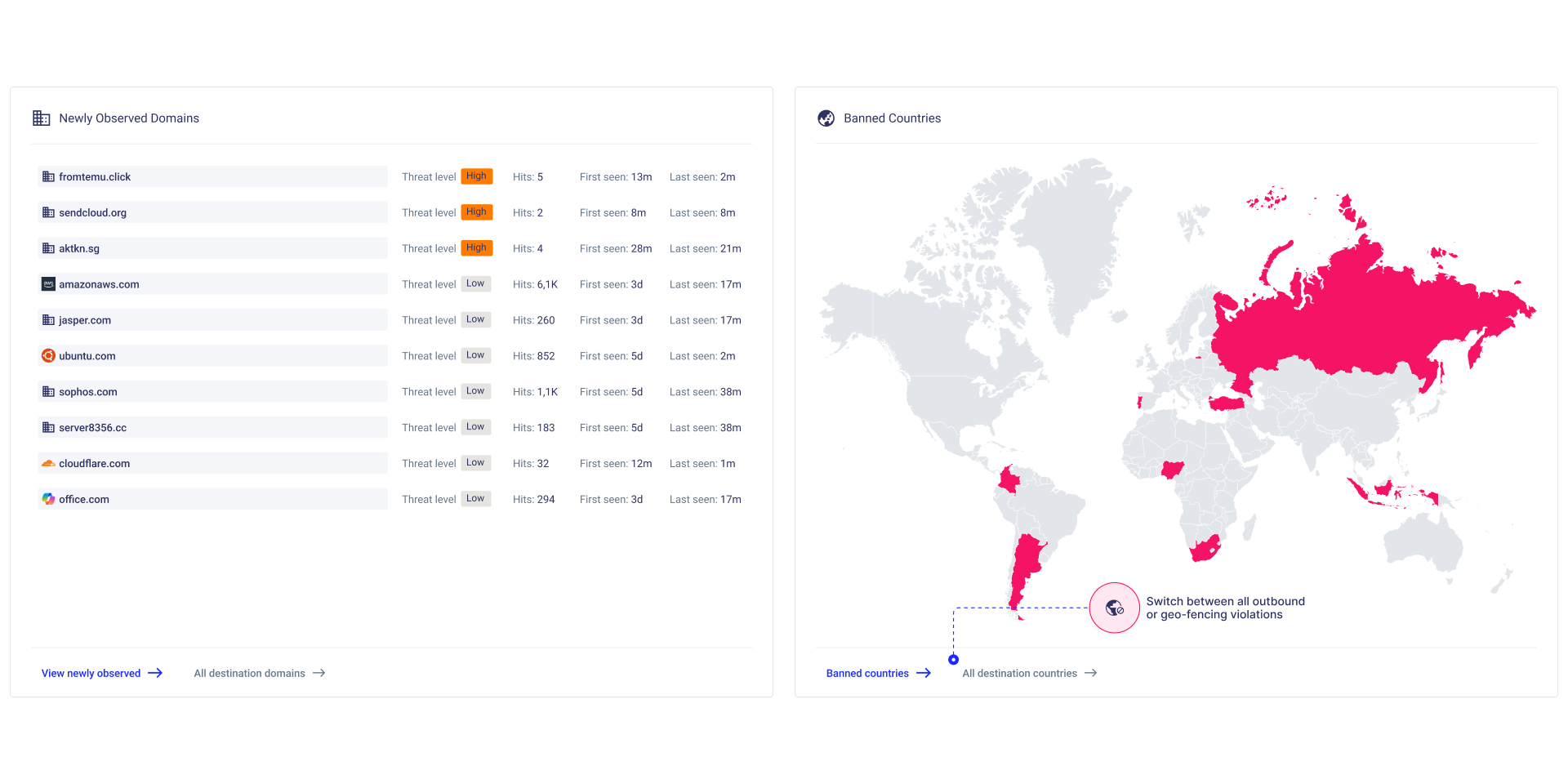
The CISO Imperative: Why Egress Traffic Control is a Strategic Security Investment
Cloud Egress traffic monitoring shifts security from reactive to proactive defense. With rising breach costs and compliance mandates, organizations cannot afford to remain blind to the traffic leaving their cloud environments. The question is not whether to invest in egress visibility, but whether you can afford the risks of going without it.
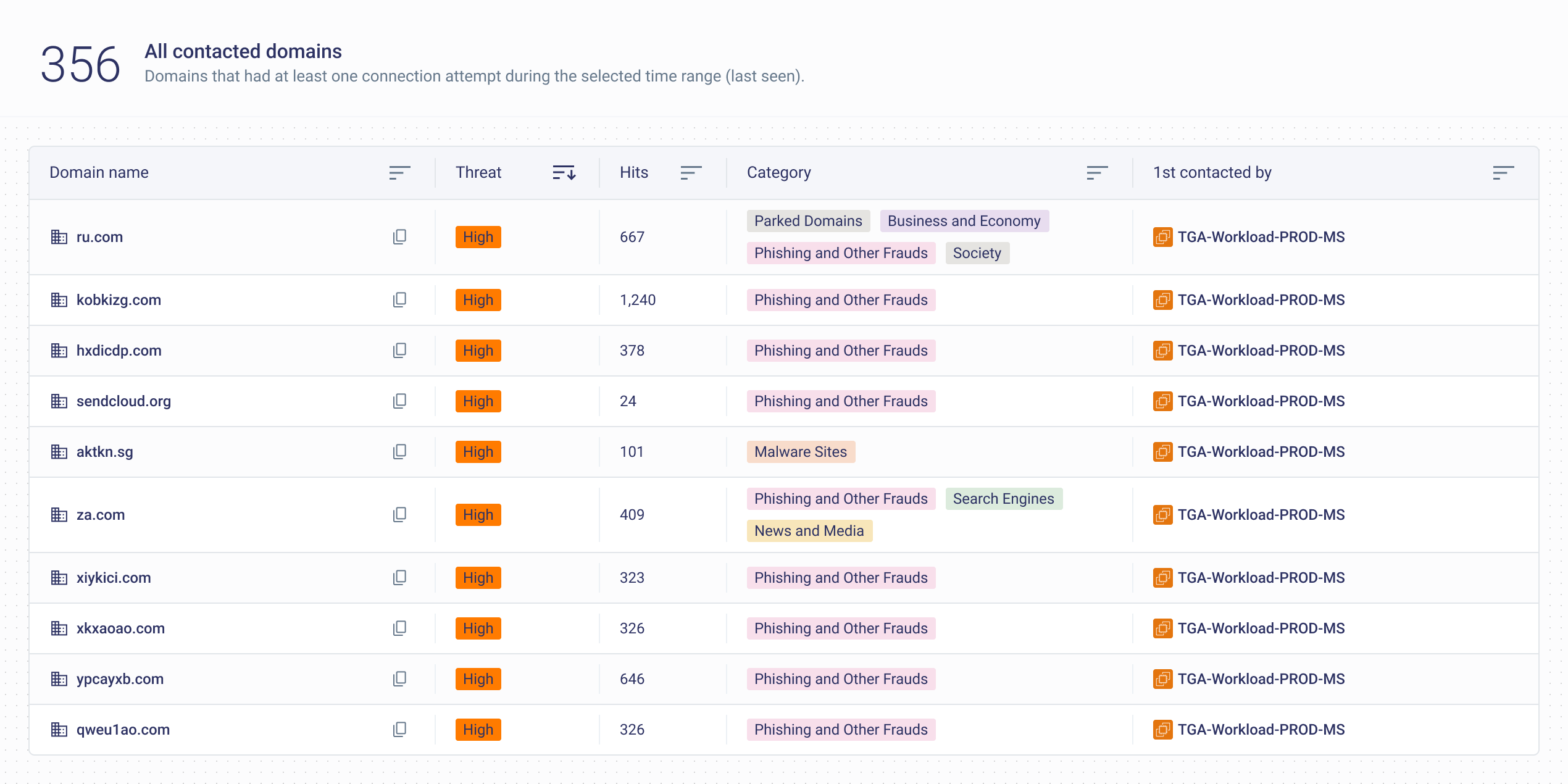
Business Case for Egress Visibility
As a CISO, I've learned that security investments must be framed in business terms. When I present egress traffic monitoring to the board, here's how I position it:
The $4.88 Million Question:
According to IBM's 2024 Cost of a Data Breach Report, the average cost of a data breach has reached $4.88 million. Yet most organizations are blind to 60-80% of their egress traffic. We're essentially flying blind during the most critical phase of an attack – data exfiltration. Hackers secretly modified a Codecov script and used it to send customer data to an external server. This breach went undetected for two months until a customer spotted the tampered script. The Codecov incident resulted in customer churn, regulatory scrutiny, and millions in remediation costs. But the real damage was reputational – a currency that takes years to rebuild and seconds to destroy.
Regulatory Reality: Compliance is No Longer Optional
From my conversations with peers across industries, egress monitoring isn't just good security hygiene – it's becoming a compliance requirement:
- PCI DSS 4.0 now explicitly requires monitoring of outbound connections from cardholder data environments.
- SOC 2 Type II auditors increasingly expect evidence of egress traffic monitoring and anomaly detection
- GDPR Article 32 mandates "appropriate technical measures" to detect unauthorized data transfers
- SOX compliance requires controls over financial data movement, including monitoring outbound transfers
When regulators ask, "How do you prevent unauthorized data exfiltration?" saying "We have a firewall" is no longer sufficient. They want evidence of continuous monitoring and behavioral analysis.
The Operational Challenge: Beyond Technology
Implementing egress traffic control isn't just a technical challenge – it's an organizational one. Here's what I've learned:
Team Readiness
Most security teams are overwhelmed with alerts. Adding egress monitoring without proper tuning creates more noise, not signal. The solution requires:
- Analyst training on DNS-based threat hunting.
- Clear escalation procedures for egress anomalies.
- Integration with existing SIEM and SOAR platforms.
False Positive Management
In my experience, poorly implemented egress monitoring generates 200+ alerts per day. Effective behavioral baselines and intelligent filtering are essential to maintain team sanity and response effectiveness.
Cross-Functional Coordination
DevOps teams often view security monitoring as friction. Success requires:
- Early involvement in CI/CD pipeline design.
- Clear communication about monitoring scope and purpose.
- Automated whitelisting processes for legitimate business traffic.
Strategic Integration: Building a Comprehensive Defense
Egress monitoring shouldn't exist in isolation. Here's how I integrate it into our broader security strategy:
Detection and Response Stack Integration
- SIEM correlation with endpoint and network telemetry.
- Threat intelligence enrichment of suspicious domains.
- Automated response capabilities for high-confidence threats.
Zero Trust Architecture Alignment
Egress monitoring is a critical component of our zero-trust implementation:
- Least privilege access based on behavioral baselines.
- Continuous verification of outbound communications.
- Dynamic policy enforcement based on risk scoring.
Security Metrics and KPIs
I track these executive-level metrics:
- Mean Time to Detection (MTTD) for egress anomalies
- False positive rate and alert fatigue indicators
- Coverage percentage across cloud environments
- Cost per protected workload
Budget Justification: The ROI of Egress Monitoring
When presenting budget requests, I frame egress monitoring ROI in terms executives understand:
Cost Avoidance
- Breach prevention: Single prevented incident pays for multiple years of monitoring
- Compliance efficiency: Automated evidence collection reduces audit costs by 40%
- Tool consolidation: Behavioral baselines reduce need for multiple point solutions
Operational Efficiency
- Analyst productivity: 70% reduction in manual threat hunting time
- Incident response: 50% faster containment through precise attribution
- Change management: Automated policy updates based on legitimate traffic patterns
-
-
Implementation Roadmap: A Phased Approach
Based on lessons learned from three egress monitoring implementations:
Phase 1: Foundation (Months 1-2)
- Enable AWS native logging across all accounts
- Establish baseline data collection and storage
- Train initial analyst team on DNS-based threat hunting
Phase 2: Intelligence (Months 3-4)
- Implement behavioral baseline algorithms
- Configure initial alerting rules with high confidence thresholds
- Begin threat intelligence integration
Phase 3: Automation (Months 5-6)
- Deploy automated response capabilities.
- Integrate with existing security orchestration platforms
- Establish continuous improvement processes
-
The Board Conversation: Communicating Egress Risk
When presenting to the board, I use this framework:
The Threat:
"We can see attackers entering our environment, but we're blind to what they're taking when they leave."
The Impact:
"A single undetected data exfiltration could cost us $4.88 million and damage relationships with customers who trust us with their data."
The Solution:
"Egress monitoring gives us the visibility to detect and stop data theft before it leaves our environment."
The Investment:
"For less than 1% of our potential breach cost, we can implement comprehensive egress monitoring across our entire cloud environment."
Lessons Learned: What I Wish I'd Known
After implementing egress monitoring at three organizations:
1. Start with high-value assets: Don't boil the ocean. Focus on crown jewel applications first.
2. Invest in tuning: Untuned egress monitoring creates more problems than it solves.
3.Plan for scale: Cloud environments grow exponentially. Ensure your solution scales with your business
4.Measure everything: Executive support requires demonstrable ROI and risk reduction metrics
-
-
-
Conclusion
From Reactive to Predictive
Egress traffic monitoring represents a fundamental shift from reactive security to predictive defense. As CISOs, we can no longer afford to discover breaches months after they occur.
The question isn't whether you can afford to implement egress monitoring – it's whether you can afford not to.
Watch a Demo
Discover how CloudFence's AI-driven engine establishes behavioral baselines, delivers real-time visibility, and detects threats before they escalate—helping your team shift from reactive firefighting to strategic cloud security management.
Stop Being in the Dark!
Watch a Demo
Discover how CloudFence's AI-driven engine establishes behavioral baselines, delivers real-time visibility, and detects threats before they escalate—helping your team shift from reactive firefighting to strategic cloud security management.
Keep Exploring Cloud Security Insights
Looking to dive deeper? Check out these handpicked articles related to cloud visibility, threat detection, and workload protection.