Understanding TCP Flags in AWS VPC Flow Logs
TCP flags are control bits in the TCP header that indicate the state and direction of TCP connections. In VPC Flow Logs, these flags are bit masks, meaning they can be combined to create unique numbers. These combinations happen when multiple requests occur within the "aggregation interval" of the flow logs.

Understanding TCP Flags in AWS VPC Flow Logs
TCP flags in AWS VPC Flow Logs provide valuable information about the state and direction of TCP connections. These flags are binary indicators represented as a decimal value in flow logs.
What are TCP Flags?
TCP flags are control bits in the TCP header that indicate specific conditions during data transmission.
In VPC Flow Logs, these flags are bit masks, meaning they can be combined to create unique numbers. These combinations happen when multiple requests occur within the "aggregation interval" of the flow logs.
The decimal value is the sum of all active TCP flags in the connection, with each flag representing a specific binary position.
Below some examples:
- FIN — 1
- SYN — 2
- RST — 4
- SYN-ACK — 18
FIN
Decimal Value: 1

SYN
Decimal Value: 2

RST
Decimal Value: 4

SYN-ACK
Decimal Value: 18

Common TCP Flag Combinations
The following table presents the most commonly observed TCP flag combinations in VPC Flow Logs.
While there are other possible flag combinations, these patterns represent the typical connection lifecycle events you'll encounter when analyzing your network traffic.

Conclusion
By analyzing TCP flags in VPC Flow Logs, you gain deep visibility into network behaviors—established connections, resets, and potential reconnaissance.
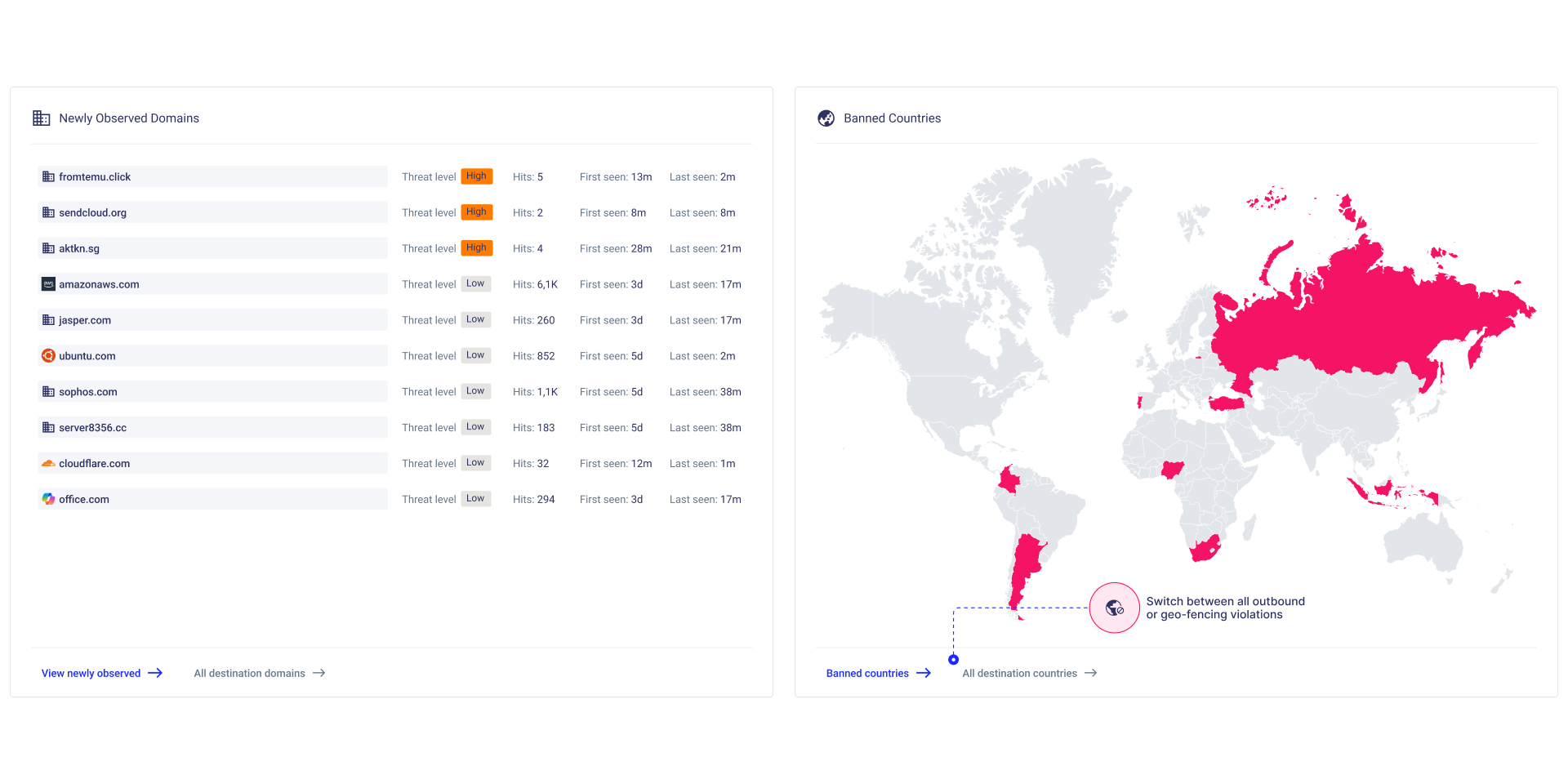
CloudFence ingests these logs into an AI-driven analytics engine that dynamically baselines every workload and surfaces anomalies within minutes, empowering your security team to spot suspicious deviations instantly. Its centralized Security Group dashboard then flags stale or over-permissive “all ports” rules and delivers precise, port-level recommendations to enforce strict least-privilege across your cloud environment.
Watch a Demo
Discover how CloudFence's AI-driven engine establishes behavioral baselines, delivers real-time visibility, and detects threats before they escalate—helping your team shift from reactive firefighting to strategic cloud security management.
Stop Being in the Dark!
Watch a Demo
Discover how CloudFence's AI-driven engine establishes behavioral baselines, delivers real-time visibility, and detects threats before they escalate—helping your team shift from reactive firefighting to strategic cloud security management.
Keep Exploring Cloud Security Insights
Looking to dive deeper? Check out these handpicked articles related to cloud visibility, threat detection, and workload protection.