AWS Security Groups: From Liability to Defense
Security Groups are too often treated as “set it and forget it.” But in a cloud-native, zero-trust world, they must be treated as dynamic controls—actively reviewed, and tied to least-privilege principles. Automating the monitoring, lock down, and pruning cycle transforms Security Groups from static risks into adaptive defenses that scale with your cloud operations.

A single misconfigured Security Group rule turned a routine Tuesday into a nightmare. An overlypermissive rule—0.0.0.0/0 on port 22—left SSH access wide open to the internet. Within hours, attackers had moved laterally through the network, accessing databases that should have been isolated.
This wasn't a sophisticated attack. It was preventable. Security Groups are often treated as "set it and forget it" configurations. But in a zero-trust world, they must be dynamic controls—actively monitored, reviewed, and aligned with least-privilege principles.
The difference between static risk and adaptive defense lies in how you manage them.
Why Security Groups Matter More Than Ever
Security Groups act as stateful firewalls at the instance level—your critical third layer of defense in a properly architected AWS environment. While Network Firewalls and Web Application Firewalls provide perimeter controls like deep packet inspection and application-layer filtering, and NACLs offer subnet-level stateless filtering, Security Groups deliver granular, stateful control to every cloud resource that lives inside a VPC.
The stakes are high:
- Overly permissive rules create direct attack paths (like the Colonial Pipeline breach)
- Wide-open egress enables data exfiltration and C2 callbacks
- Orphaned Security Groups become forgotten vulnerabilities
- Poor visibility makes auditing nearly impossible
The practice, known as the principle of least privilege, directly limits the number of pathways an attacker could exploit in the event of a breach, thus greatly limiting potential damage.
Beyond security, enforcing least privilege is also essential for meeting regulatory requirements. Frameworks like SOC 2 and HIPAA require demonstrating that network access is:
- Provisioned on a need-to-know basis.
- Regularly reviewed.
- Promptly revoked when no longer necessary.
Common misconfiguration that create risk:
- Using Default Security Groups with broad rules
- Wide Port Ranges or granting access to Large Subnet or VPC Ranges
- Security Group rule chains - if not used properly create a false sense of restriction; traffic may appear limited, but overly permissive referenced groups can allow broad access creating hidden paths for lateral movement or unintended exposure.
- Cross-account Security Group references without proper governance
The Three-Phase Approach to Security Group Hardening
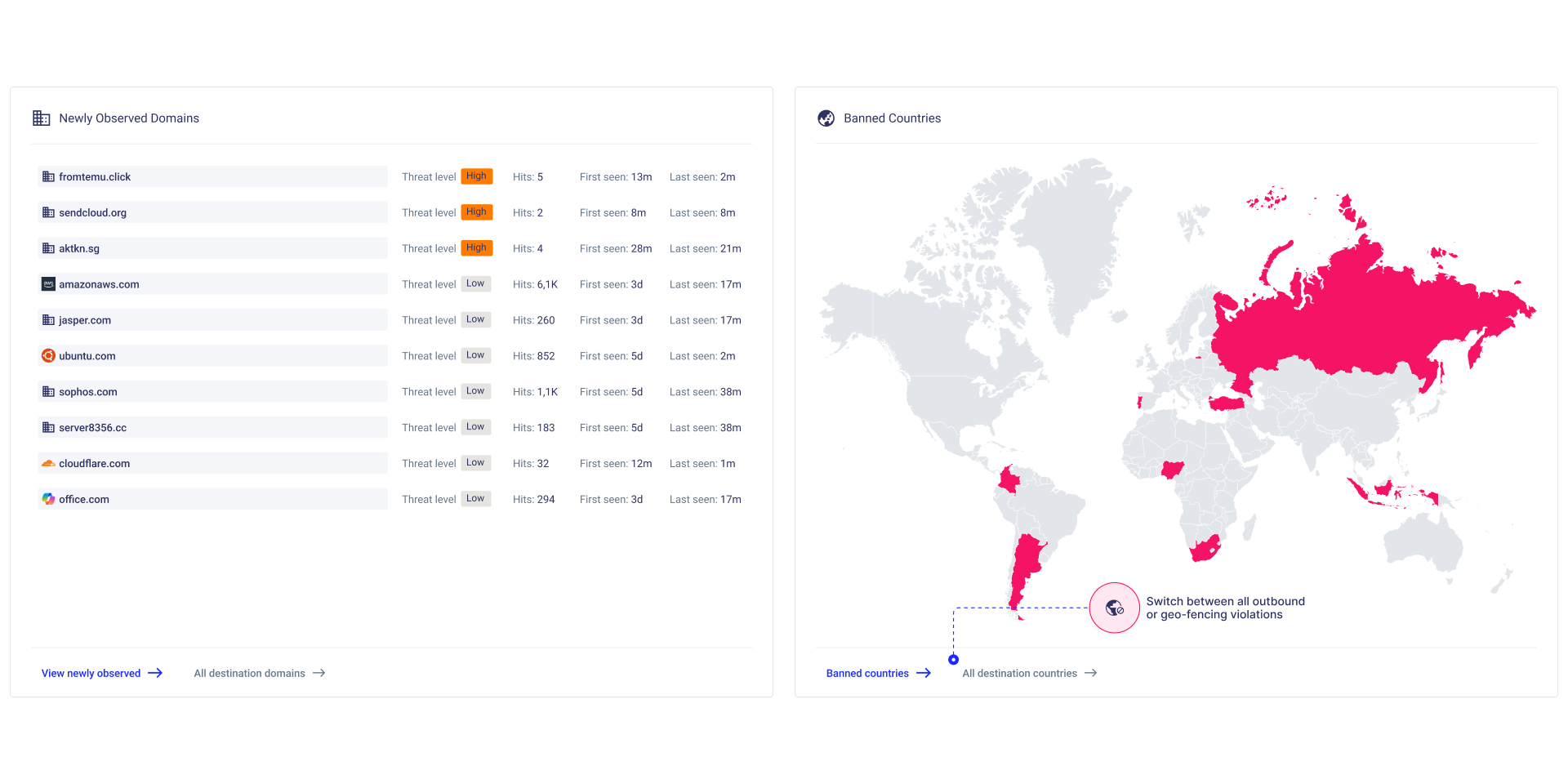
Phase 1: Visibility—Know What You Have
Your goal in this phase is to build an inventory of all Security Groups across accounts , and Identify unexpected or undocumented SG or connections between systems (e.g., frontend talking directly to DB). Visualize how workloads communicate (east–west traffic) and Highlight any instances or Security Group with Wide open access. In other words, Identify and prioritize what needs attention in the next (Lock Down) phase.
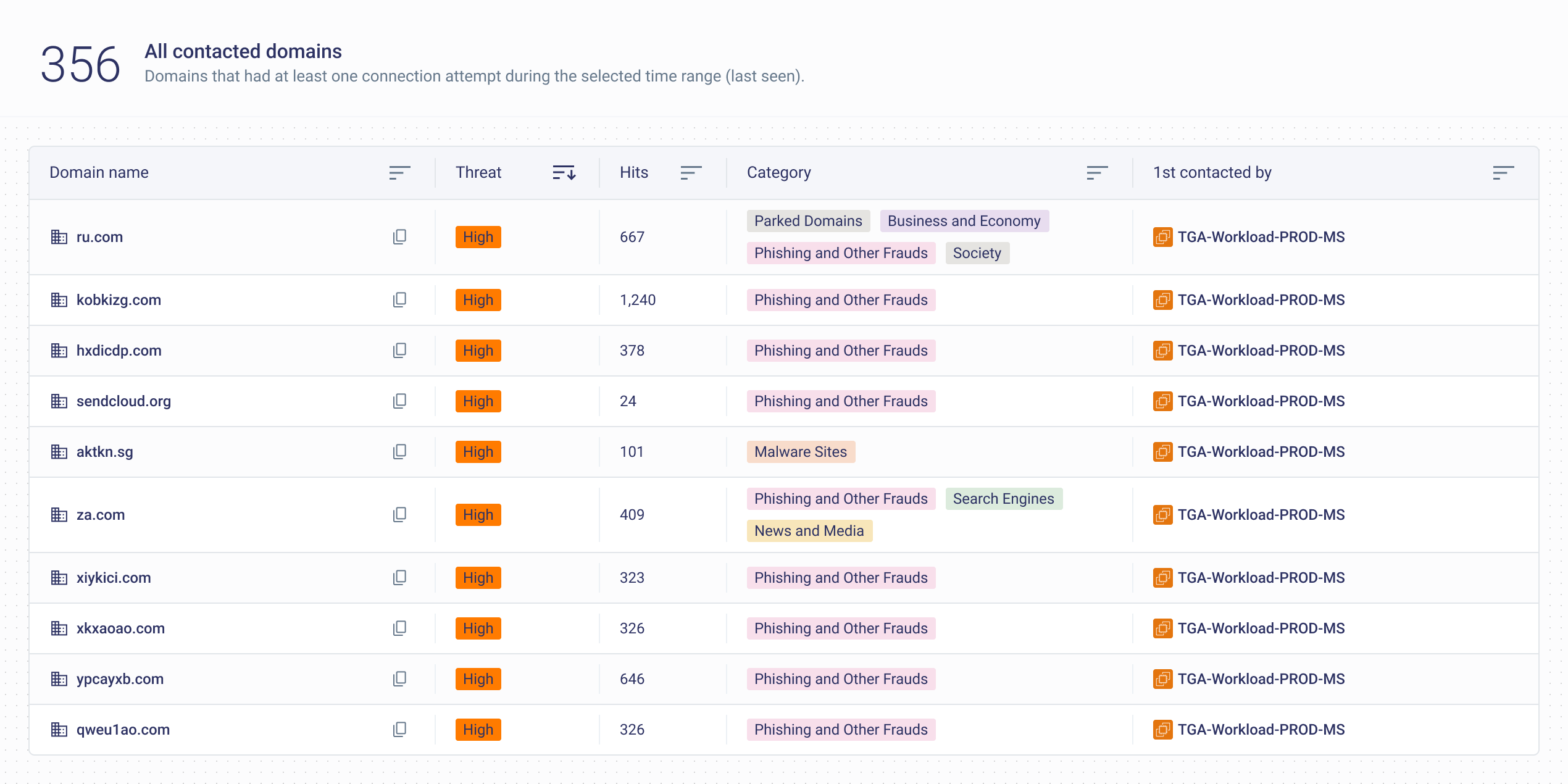
Traditional firewalls show which rules are used; Security Groups don’t. This blind spot makes it nearly impossible for DevSecOps teams to audit which rules are actually needed. To close this gap, you must enable cloud-native network logs like AWS VPC Flow Logs and use tools such as AWS Config Rules and Security Hub to flag risky settings. But these tools only catch misconfigurations—they can’t tell you which Security Group rules are truly necessary, since they don’t match traffic against the rules.
To pinpoint unused or excessive rules, you need to analyze flow logs with AWS Athena—or let CloudFence automate the entire process, end to end
- Build an inventory of all Security Groups across accounts and regions, and what resources (EC2, ALB, Lambda ENIs) are attached to them.
- Classify by risk: Start with Security Groups that pose direct exposure or lateral movement risk , such as those with:
- Internet facing exposure - 0.0.0.0/0 to sensitive ports such as SSH (22), RDP (3389), DB ports (3306, 5432, 1433).
- All Traffic or wide port ranges (e.g., 0–65535).
- Attachment to critical resources
- Attachment to many resources — one misconfigured rule could impact dozens of instances.
- Identify unused assets: Orphaned Security Groups and rules with no traffic over 30+ days.
CISO Insight
The visibility phase isn’t about finding and fixing everything—it’s about creating clarity. It sets the foundation for every future action. Without this step, any “lock down” effort risks breaking things or missing critical exposures. Think of visibility not as a report, but as an ongoing practice.
Phase 2: Lockdown—Eliminate Obvious Risks
The goal of the Lockdown phase is to translate insight into action—turning visibility into tangible risk reduction. This means systematically tightening overly permissive Security Group Rules. It’s about enforcing the principle of least privilege: restricting access to only what is needed, from only who needs it, for only as long as it's needed.
1. Remove Orphaned Security Groups
Removing orphaned Security Groups—those not attached to any resources—is a low-risk, high-impact first step in tightening your cloud network security. While they may seem harmless, orphaned Security Groups often contain outdated or overly permissive rules and can be mistakenly reassigned without scrutiny. They clutter your environment, create audit noise, and increase your risk of accidental exposure.
2. Tighten High-Risk Rules
Focus on Security Groups with:
- 0.0.0.0/0 access to sensitive ports
- "All traffic" rules
- Broad internal access without business justification
To identify and prioritize these rules effectively, it’s essential to enable VPC Flow Logs and gather the last-used timestamp and hit count for each rule. This visibility ensures that decisions are made with clarity—reducing risk without breaking legitimate access.
3. Apply Least Privilege to Egress Rules
Don't ignore outbound traffic. Overly permissive egress enables:
- Data exfiltration
- Command-and-control callbacks
- Lateral movement to internal and external services
Restrict egress access to only required IPs, domains, or services your applications actually need.
4. Clean up Unused Rules
Use your VPC Flow Logs analysis to identify rules with no traffic over a defined period (30-90 days). Remove them systematically.
CISO Insight
The lockdown phase is where visibility turns into measurable security gains. This is not about perfection—it’s about systematically removing the most obvious, fixable risks first.
Phase 3: Automation Phase - Make it Scalable
The goal of this phase is to shift from cleanup to control—ensuring that future Security Groups are created with proper context and accountability to prevent the same issues from reoccurring.
1. Integrate Security Group changes with approval systems
Engineering teams shouldn't modify high-risk Security Groups without review. Implement approval workflows for:
- Changes to internet-facing Security Groups
- Rules affecting sensitive ports
- Modifications to Security Groups attached to critical resources
2. Integrate Security Group changes with approval systems
Manage Security Groups through CloudFormation or Terraform to ensure consistency and prevent configuration drift. This eliminates the "click-ops" that often introduces security gaps.
3. Enforce Tagging and Ownership for Lifecycle Management
Security Group rules can easily outlive their original purpose, especially in dynamic cloud environments.
Without clear ownership and tagging, they become difficult to track and review. Require tags for:
- Owner: Who's responsible for this Security Group?
- Environment: Production, staging, development
- Expiration: When should this access be reviewed?
- Purpose: Why does this rule exist?
4. Schedule Reviews
Cloud environments change fast. Rules that were valid last month can become unnecessary or risky. Automate quarterly reviews of:
- High-risk Security Groups
- Rules approaching expiration dates
- Security Groups with recent changes
5. The Path Forward
Security Group hardening isn't a one-time project—it's an ongoing practice. Start with visibility, focus on high-risk eliminations, then build automation to prevent regression. The goal isn't perfection—it's progress.
Every overly permissive rule you eliminate reduces your attack surface. Every automated control you implement scales your security posture. In the cloud, Security Groups can either be your weakest link or your strongest defense. The choice is in how you manage them.
Your immediate next steps:
- Enable VPC Flow Logs if not already active
- Inventory Security Groups allowing 0.0.0.0/0 access
- Identify and remove orphaned Security Groups
- Implement approval workflows for sensitive changes.
CISO Insight
The Automation Phase is about making security scalable and repeatable. Cleanup is important—but without strong controls around change, ownership, and enforcement, the same risks will return.
Beyond Defense: Security as a Business Enabler
At CloudFence, we believe security should accelerate your business, not slow it down. Automating least privilege at the network layer doesn’t just shrink your attack surface — it simplifies audits, reduces operational noise, and empowers engineers to deploy confidently.
The Path Forward
I invite you to think beyond ad-hoc cleanups. Think about transforming your Security Groups into dynamic, continuously governed, least privilege enforcers that adapt as fast as your cloud evolves.
If attackers get in, make sure they go nowhere!
Conclusion
Achieving least privilege in Security Groups isn’t a one-time cleanup, it’s an ongoing process of visibility, control, and automation.
Security Groups aren’t going away. But how you manage them will decide whether they become your biggest liability or your strongest defense.
Watch a Demo
Discover how CloudFence's AI-driven engine establishes behavioral baselines, delivers real-time visibility, and detects threats before they escalate—helping your team shift from reactive firefighting to strategic cloud security management.
Stop Being in the Dark!
Watch a Demo
Discover how CloudFence's AI-driven engine establishes behavioral baselines, delivers real-time visibility, and detects threats before they escalate—helping your team shift from reactive firefighting to strategic cloud security management.
Keep Exploring Cloud Security Insights
Looking to dive deeper? Check out these handpicked articles related to cloud visibility, threat detection, and workload protection.