Own Your Cloud Egress Before Attackers Do
Outbound traffic is one of the most under-monitored and least controlled paths in the cloud. Cloud Security teams have focused on hardening inbound traffic, yet outbound traffic remains largely unmonitored and under-protected. Once inside, attackers move laterally and exfiltrate data through what looks like legitimate traffic. Without visibility & control on where your workloads are connecting, data exfiltration, C2 callbacks, and DNS tunneling can go completely unnoticed.
Are You Watching What’s Leaving your cloud ?
On the 31st of January 2021 Attackers gained access to Codecov’s private Docker image repository through a leaked credential. They modified the Bash uploader script used by thousands of customers. They inserted a single line of code that quietly sent all environment variables —often containing API keys, tokens, and secrets—to the attacker-controlled server via a simple curl command.
The attack unfolded silently from Codecov customers’ environments.... every time the compromised Bash uploader ran in a CI/CD pipeline, it initiated an outbound HTTP request that exfiltrated sensitive environment variables to the attacker-controlled server.
There was no malware, no inbound exploit, just unmonitored outbound communications. The attack continued for months without detection…
Egress traffic is often the last mile of security and the least controlled. Without visibility into where your workloads are reaching out, you can’t identify suspicious behavior, enforce least-privilege access, or stop data from flowing to the wrong destination.
Why Existing Tools Fall Short in the Cloud
Firewalls Don't Scale in the Cloud
The idea that you can place firewalls at every exit point in the cloud is outdated. And even when you do, firewalls rely on static rules and raw IP data, offering no sense of what’s normal or risky. This is especially dangerous in modern environments where workloads are dynamic, distributed, and ephemeral.
You can’t protect what you can’t understand; this means unusual outbound activity often goes unnoticed in your environment until it’s too late.
CSPM/CNAPP Can't Help
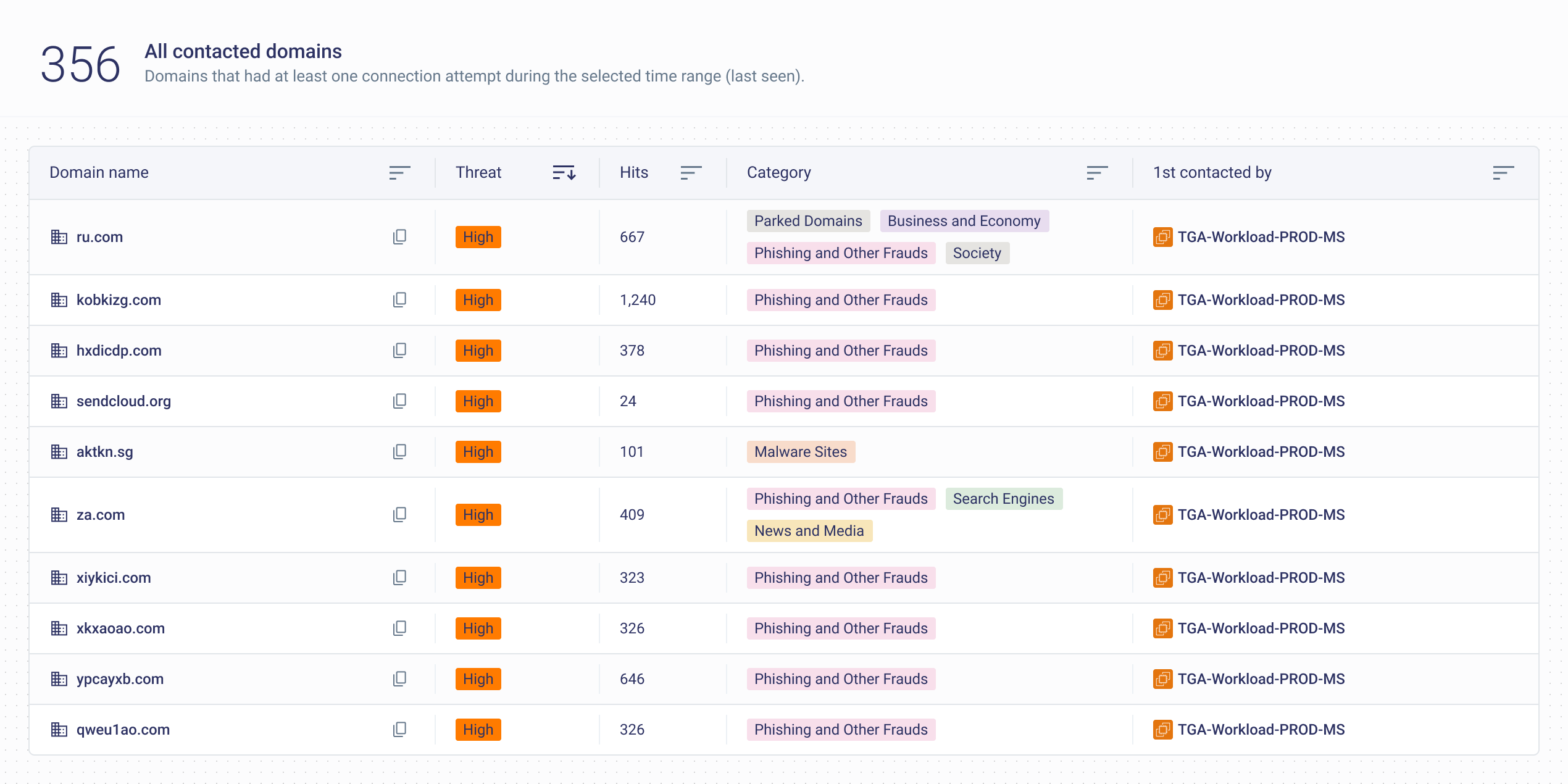
CSPM and CNAPP platforms may alert you that a security group allows egress to 0.0.0.0/0, but they have no way of telling you what’s actually happening:
- Are these rules used?
- Which workloads are making outbound requests?
- What domains are they contacting, and why?
The Shift: From Static Rules to Behavioral Baselines in your Cloud
If you want to catch egress threats early, you need to understand behavior. This means:
- Seeing every DNS request in your cloud environment.
- Knowing which workloads initiated which connections.
- Establishing a baseline for what "normal" egress looks like.
- Automatically identifying new, rare, or suspicious destinations.
1. Get Complete DNS-Level Visibility Across your AWS environment
Start by enabling and centralizing Route 53 DNS query logs and VPC Flow Logs across all accounts and regions.
Why it matters:
- Attackers abuse DNS to hide exfiltration and C2 channels.
- Domain-level monitoring gives more context than raw IPs.
- AWS-native logs allow inspection without deploying agents.
2. Attribute Outbound Connections to Specific Workloads
Seeing that traffic left your cloud isn’t enough. You need to know who sent it, and whether that behavior is expected.
3. Define Baselines for “Normal” Egress Behavior
Once visibility and attribution are in place, define what normal looks like:
- Which domains or destinations are contacted regularly?
- Which services generate that traffic?
What to do:
- Automatically build baselines using historical logs
- Flag first-time or rare destinations
- Monitor for behavior changes
4. Detect and Prioritize Rare, New, and Suspicious Destinations
Not every rare domain or IP is malicious—but many targeted attacks begin with a connection that falls just outside the norm. Detecting these outliers requires the ability to highlight deviations from expected behavior.
Why it matters:
- Rare destinations often indicate C2 or exfil activity
- Fast detection & triage means faster containment
What to do:
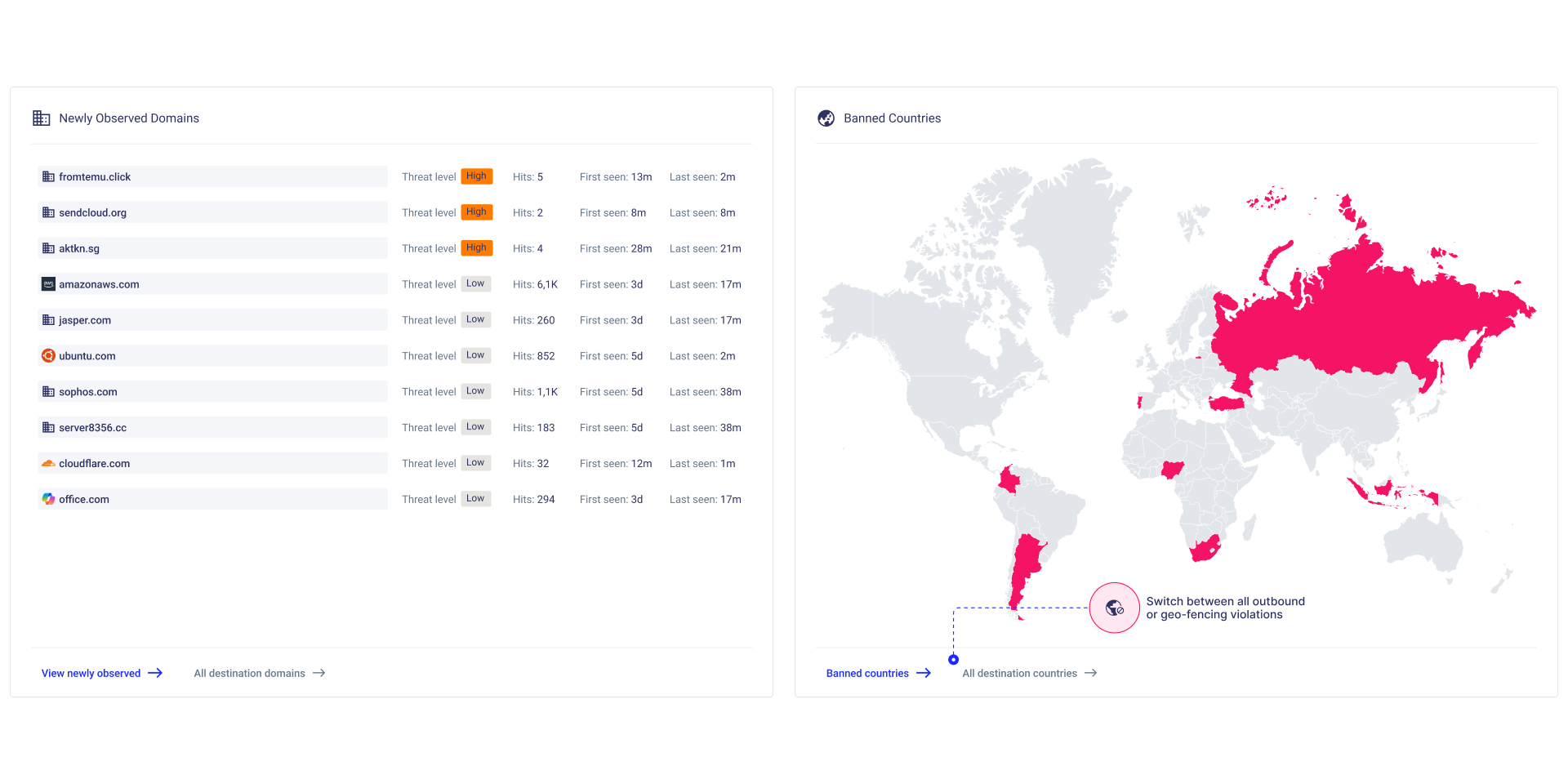
- Setup alerts for newly seen domains.
- Investigate domains with unknown or suspicious categorization.
- Investigate hardcoded direct IP connections without any corresponding DNS resolution.
- Flag workloads bypassing internal DNS resolvers.
CloudFence lets you see what’s leaving your cloud and stop what shouldn’t be going out.
CloudFence provides real-time, domain-level visibility into egress activity—without deploying agents or mirroring traffic.
We ingest cloud-native logs like VPC Flow Logs, AWS Route 53 DNS logs to:
- Detect newly observed or rare domains.
- Flag behavior that deviates from historical baselines.
- Establish least-privilege egress policies based on behavior.
Conclusion
Outbound traffic remains one of the least controlled paths in the cloud.
Shift from static rules to behavioral baselines to understand what "normal" egress looks like and automatically detect new, rare, or suspicious destinations.
If you’re serious about cloud security, you need to start watching what leaves your environment, Not just what enters.
See What’s Leaving Your Cloud
Watch a Demo
Discover how CloudFence's AI-driven engine establishes behavioral baselines, delivers real-time visibility, and detects threats before they escalate—helping your team shift from reactive firefighting to strategic cloud security management.
Stop Being in the Dark!
Watch a Demo
Discover how CloudFence's AI-driven engine establishes behavioral baselines, delivers real-time visibility, and detects threats before they escalate—helping your team shift from reactive firefighting to strategic cloud security management.
Keep Exploring Cloud Security Insights
Looking to dive deeper? Check out these handpicked articles related to cloud visibility, threat detection, and workload protection.