From Visibility to Enforcement
Continuously eliminate unused and wide-open access
CloudFence continuously reviews your security groups using real traffic patterns, automatically identifying and removing unused or overly permissive rules to tighten access and reduce risk.
Most teams audit Security Groups by looking at configuration — but that only tells half the story

Infrastructure Teams Lack Application Insight
Infrastructure teams are often unaware of application behavior, leading to the provisioning of infrastructure with wide-open network access. This creates a massive attack surface, making lateral movement and data exfiltration significantly easier for attackers.

Cloud Agility Outpaces
Security Controls
Applications in the cloud are inherently more dynamic—access that is needed today may become obsolete tomorrow due to changes in application architecture or access patterns. Without proper Cloud Network Security controls to automatically detect and restrict unused access, security teams are left with the tedious task of manually tracking and revoking unused access.

No Metrics, Painful Security
Audits
Unlike traditional on-premise firewalls, security group rules do not come with a 'hit counters' or 'last used' timestamps. This lack of cloud visibility makes it difficult for Devops teams to identify unused access rules and remove them. Reviewing Security Groups along with the matching flow logs, could take your team weeks, if not months.
Continuous Cloud Network Analysis and Access Control with CloudFence
CloudFence is an agentless solution that continuously analyses cloud network logs, such as AWS VPC flow logs and Azure NSG flow logs and cross-checks every communication to each workload against its security group configuration to Identify and remove unused access
Tighten Cloud Network Access in Minutes, Not Weeks
See all your security groups, identify risky configurations, and track unused or wide-open rules — so you can tighten network access and reduce exposure in minutes, not weeks.
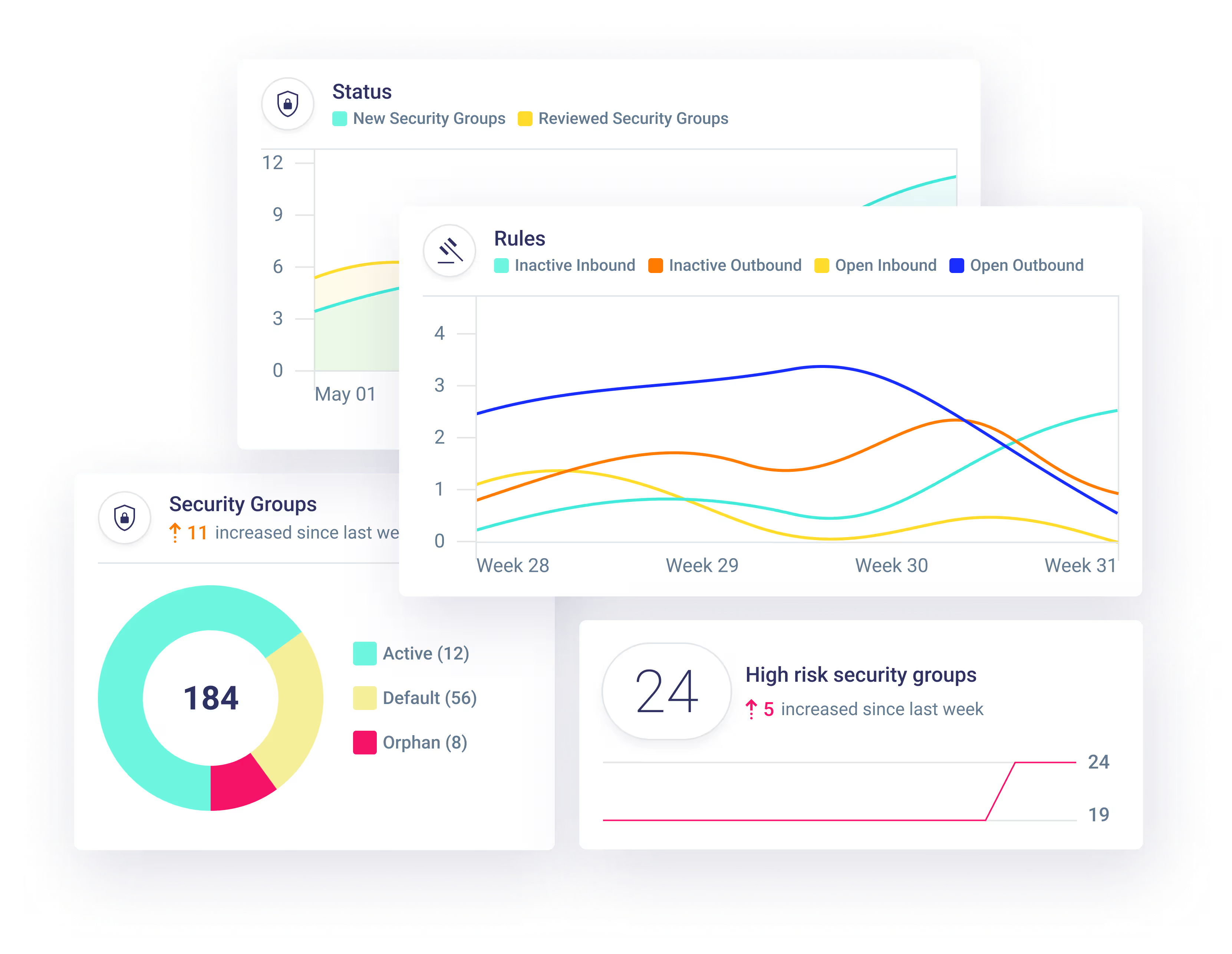

Gain Actionable Insights into Every Security Group Rule
Get detailed insights into each security group rule with last active timestamps and hit counts. Quickly identify unused rules or tighten overly permissive ones to reduce attack surfaces and hinder lateral movement.


