Know what normal looks like in your cloud & stop anomalies before they escalate into attacks
CloudFence Security engine continuously learns and establishes network and identity behavior baseline of every asset in your cloud, and helps you swiftly detect and stop suspicious behavior deviations before they become breaches.

The stealth attack reality
Attackers are already inside your cloud for weeks before you know it.
TOP 10
Limited Visibility on activities is among the TOP 10 Threats in the Cloud, and Monitoring logs without behavioral context is just expensive noise

The stealth attack reality

The visibility gap on Egress traffic

The cloud network swiss cheese problem
Unlock the full potential of your cloud logs. Gain complete visibility and detect anomalies.
CloudFence delivers agentless, AI-driven cloud network and workload-identity security by transforming native cloud logs (VPC Flow logs, CloudTrail, Route53 DNS logs,.. ) into real-time threat and behavior anomaly detection.
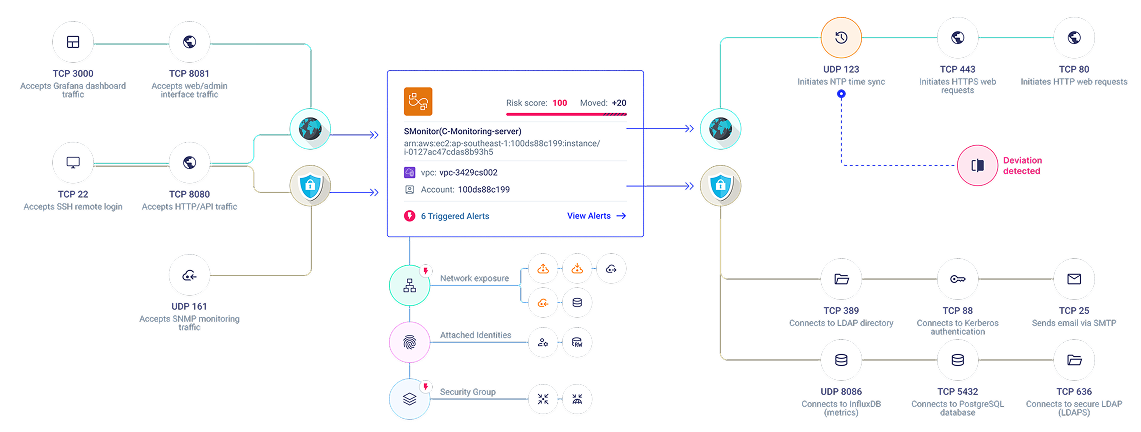
Understand what’s normal so you can catch what’s not
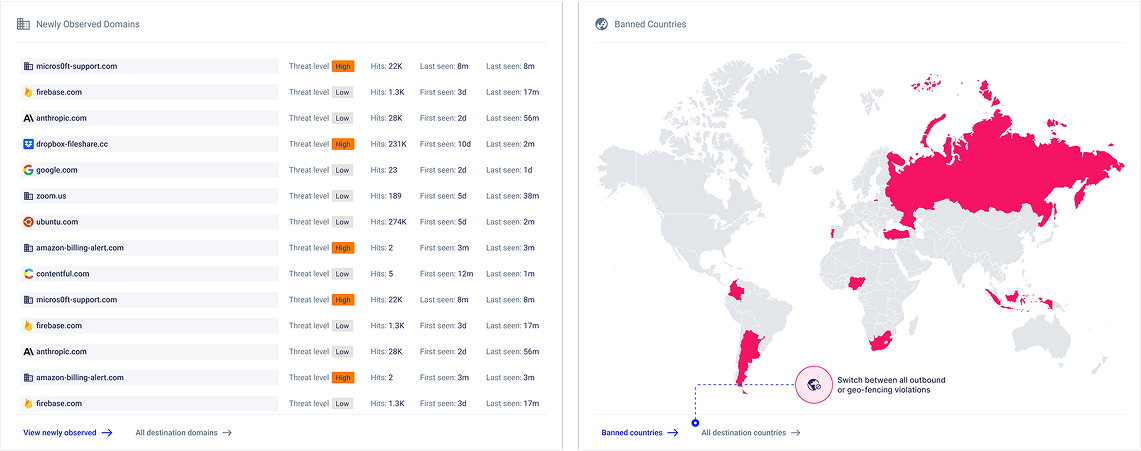
See what’s leaving your cloud and control it
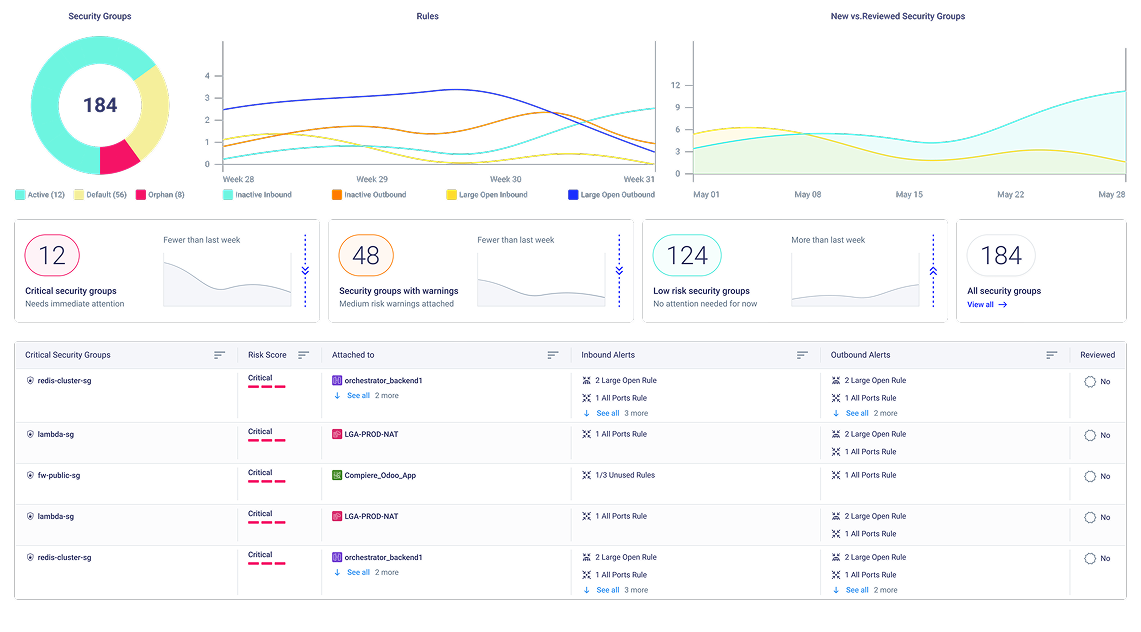
Shrink your network attack surface automatically
Make sense of your complex cloud footprint visually, in real time
CSPM and CNAPP focus on misconfigurations and posture especially Ingress. CloudFence focuses on behavioral detection — it learns normal patterns for every workload by looking at network and identity logs, builds baselines, and flags suspicious deviations in real time, especially in outbound traffic. It complements posture tools by catching what static config oriented checks miss.
SIEMs collect and store logs but rely on manual rules and tuning to find threats. CloudFence automatically analyzes network and identity behavior, builds per-workload baselines, and detects unusual activity without rule engineering — delivering fast, focused, actionable detections purpose-built for the cloud.
CloudFence itself focuses on detection and visibility, not inline blocking. However, it can integrate with your cloud controls (like security groups, firewalls ) to automate response actions or trigger blocking through your existing infrastructure.
CloudFence charges a flat yearly fee, based on the number of workloads with active interfaces generating traffic. This model provides cost predictability, eliminates surprises, and scales with your actual environment. Integration and hosting are fully managed, and we offer unlimited seats for your security and operations teams.

Take control of your cloud security before threats do.
Don't let invisible risks compromise your cloud infrastructure. CloudFence provides the visibility and proactive protection your security team needs to detect, prevent, and stop potential threats before they become full-blown attacks.




